Advantages of using SSO
Using SSO for user authentication makes lives easier for stakeholders, Condens admins and IT admins.
Stakeholders don't need to manually create an account for Condens, instead they can authenticate with one click.
Condens Admins don't need to invite Stakeholders manually one by one. Instead, with SSO they can give a certain group or anyone in the organization access to Condens automatically.
IT admins centrally manage user access. If, for example, someone leaves the organization, IT can revoke access to all their accounts including that of Condens.
Single Sign-On also supports the implementation of two-factor authentication (2FA) or multi-factor authentication (MFA) for an added layer of security.
How to enable SSO
Go to Settings, click on "Security & Login" and select "Enable Single Sign-On".
Create the application in the identity provider. Here you can find the specific guide to follow for your SSO provider:
Copy the following information from your SSO provider into the respective cells:
IdP Login URL
IdP Entity ID
Certificate
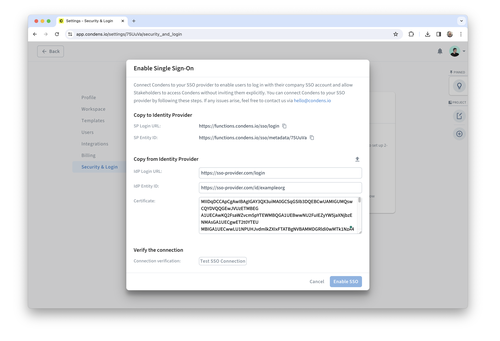
Make sure that there is at least one user that is part of the SSO application with which you can log in (required for testing).
Verify the connection by clicking on "Test SSO Connection"
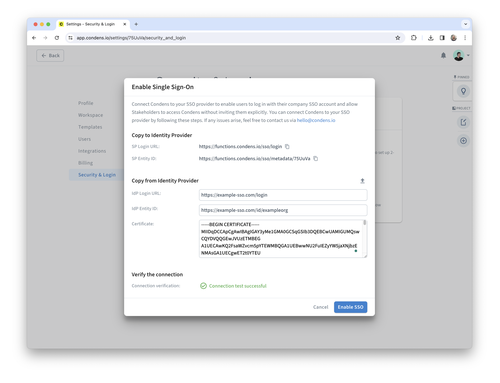
Once the connection test is successful you can enable SSO.
Once SSO is enabled, you will see a “Connect to SSO” notification at the top of your screen that allows you to connect your current email/password account to your SSO account. We recommend doing that to ensure everything is set up correctly.
If you want to show the same “Connect to SSO” notification for all users in your account you can click the
icon next to the adoption information.
You can also check which users have switched to using SSO by clicking on the
icon next to the adoption information.
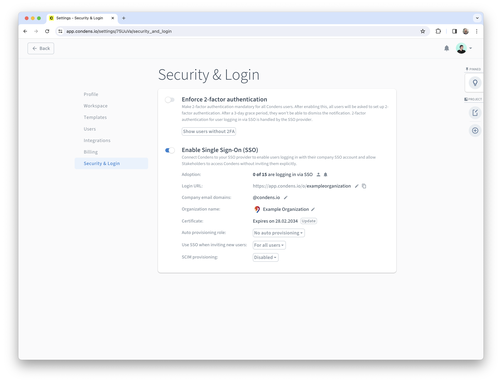
Configuring SSO
Login URL
Each SSO configuration in Condens has its own login URL. They all have the form https://app.condens.io/o/<yourcompanyname>. You can edit the last part of the URL. Usually, it’s a good idea to use your company name for that.
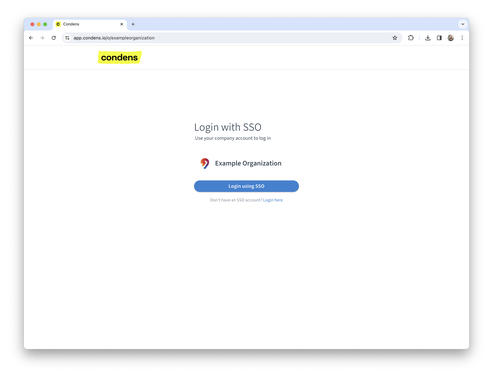
Share this URL with your colleagues to make it easy for them to log into your company’s Condens account.

You can customize the login page by editing the company name at the top of the “Security & Login” settings or by uploading a logo there.
Company email domains
Make sure to list all the email domains your colleagues who should use SSO might use. That way, Condens will know to redirect them to your company’s login page if they try to log in using their email. You can add domains to that list by clicking on the edit button. Please note that you can only add domains that are used by at least one user in your account, to make sure that you have access to these domains.
Auto provisioning
By default, only users that are invited to Condens can join. If Auto provisioning is enabled, any user who is part of the SSO application can log in to Condens. Under “Auto provision role”, the role that they get assigned can be configured. Please note that users who are explicitly invited still get the role that was selected when inviting them. Researchers and Administrators have to be invited manually to view and edit raw data.
The auto provisioned role of a user can also be changed at any point once have logged in.
It is also possible to set the role of a newly provisioned user based on a SAML attribute. For that, under “Auto provision role” select “Based on SAML attribute”. Then you have to enter the name of the attribute and which value maps to which role in Condens.
Selective SSO
By default, once SSO is enabled all users invited into Condens are invited via SSO. This can be changed by setting the value for "Use SSO when inviting new users” to “Only for company email domains”. That way, SSO is only used if the email address of the invited user matches one of the company email domains. If it doesn’t, the user can use email and password to log in.
SCIM Provisioning
Condens also supports the SCIM protocol for synchronizing users between the SSO provider and Condens. It can be enabled by selecting “SCIM provisioning”: “Enabled”. Condens supports GET, POST, PUT and PATCH operations. The following attributes can be changed via SCIM: roles, active, name, and email (via userName).
